Welcome to the third installment of our “Bowtie Analysis Blog” series. In our first installment, we talked about the usefulness of risk bowties for training employees on workplace risks, and our second installment explored the way risk bowties can pull together information from many different types of assessments.
In this post, we’ll be looking at the ways risk bowties simplify our ability to manage and verify the effectiveness of our risk controls.
A Brief Overview of Risk Controls
In our previous installments of this series, we talked about how risk bowties help us to gain an accurate view of our risk pathways, helping us see (for example) that there are often multiple causes associated with a single unplanned event, as well as multiple possible consequences. The intuitive visual organization of the risk bowtie gives us a fuller understanding of the complexity of risk pathways and restrains us from the temptation that is common with tabular risk assessments, such as spreadsheets, of seeing all pathways as simple and linear.
But that’s just the start. Once you’ve identified all potential risk causes and impacts, you can then begin developing and assigning the appropriate risk controls to eliminate or reduce them. Luckily, as we’ll see, risk bowties are a big help here, too.
Risk controls can include a variety of measures, such as engineering and process design improvements, training, work practices, administrative policies and any other measure that acts in some repeatable and reliable way to minimize the likelihood and/or severity of risks.
When planning which controls to use, we should refer to the NIOSH Hierarchy of Controls, which we show below.
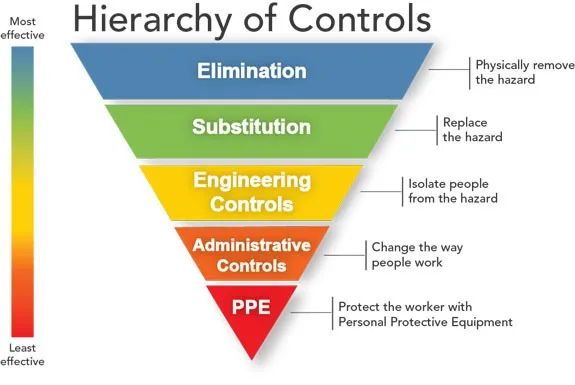
The key takeaway from this diagram is that the most effective controls are those which actually remove the source of risk through either elimination or substitution, and then use the remaining controls in descending order of preference to reduce residual risk to acceptable levels. Personal protective equipment (PPE) is a last resort because it only creates a barrier between the worker and the source of risk. The effectiveness of PPE also depends on a number of factors, such as proper selection of which equipment to use, its maintenance and training for employees using it.
Types of Controls
We classify controls based on the specific functions they play within our risk pathways. The different kinds of risk controls can be categorized as follows:
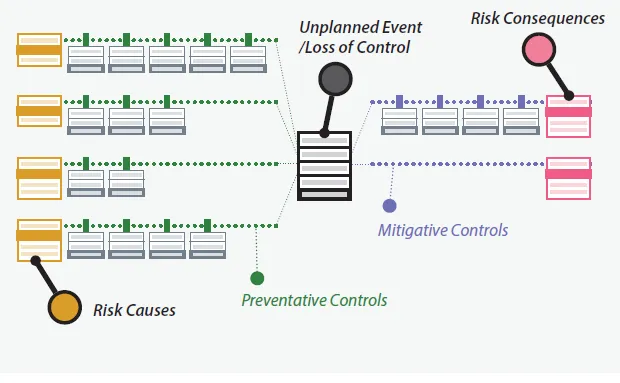
Preventative: These are controls we design and put in place to prevent a specific accident or “top event” from happening. At the point of “loss of control” where the top event occurs, we now must rely on our next category of mitigative controls.
Mitigative: These are controls we put in place to control the consequences of an unplanned event if it still happens in spite of our preventative controls. Mitigative controls can further be broken down into:
- Detective: These controls are used to detect failure of preventative controls and the onset of a top event as soon as possible, to give us the best chance of acting quickly to reduce the severity of consequences.
- Reactive: These controls that directly react to a top event and attenuate its consequences.
Be sure to take sufficient time to evaluate potential alternative controls for adequacy, reliability and other key risk indicators (KRIs), in order to select the most effective controls for specific causes and impacts. You should always consider the possibility of implementing multiple controls for individual causes or impacts. Doing so helps to create additive layers of protection against risks.
Many people who manage risk using tabular data have difficulty getting the information on all risk controls in one place. Risk bowties make that much easier to do, so that the safety professional can then get a clearer idea of how to verify that controls are effective. For example, the user can easily see that all preventative controls are on the left side of the top event, and all mitigative controls are on the right side, as we see in the diagram below.
The Simple Way to Manage Controls
If you have a single software system that creates and manages risk bowties, as well as critical controls verification, you’re going to have a much easier time connecting these key parts of your risk management system. Once you’ve fully populated your risk bowties with appropriate preventative and mitigative controls, you’re ready to start planning for critical control assurance activities.
Setting up verification activities is fairly straightforward and builds on the knowledge acquired during the risk analysis process. The greater visibility and understanding of risk pathways gained by creating our bowties helps to get us primed and ready for this step. You’ll most likely already start getting a good idea of which groups of critical controls or “base controls” you’ll need while you’re identifying and analyzing risk scenarios. At this point, you’ll also probably be able to see which particular types of scenarios would be catastrophic “major accident events,” and deserve special attention.
From there, critical controls verification capabilities within the software give you the accessibility you need to view all your controls throughout your operations. You’ll also be able to confirm that controls were installed as planned and that they are effective at delivering the expected level of risk reduction.
Taking the time to configure these factors during risk analysis sets the framework for greater efficiency down the track. If done correctly, you can automatically generate inspection or audit tools that target your critical controls or major accident events. Setting up base controls also reduces the complexity of bowtie diagrams, by reducing the number of seemingly unique risk controls in play.
Looking for More Information?
If you’re looking for more information on risk bowties, we’ve got you covered. Here are just some of our growing collection of resources:
- If you want a really deep dive into risk bowties, register for our upcoming 8-hour Bowtie Analysis Training Course, split into two afternoon sessions. We’ll cover the linkages between risk causes and consequences, closely examine the role of control selection and verification, and discuss how risk bowties can help you and your team share a common understanding of risk and engage in best management practices.
- If you’re just looking for a quick guide to learn more about risk bowties and how they can help you develop a comprehensive view of risks which can easily be kept updated and used to train your workforce, download our risk bowties infographic.
And of course, please check out the fourth installment of our “Bowtie Analysis” blog series!
Let VelocityEHS Help!
Our customers consistently report that our bowtie analysis capabilities have helped them achieve dramatic improvements to workplace productivity, knowledge sharing and risk management program performance.
Bowtie analysis is just one of many tools within our Risk Management solution, which also includes risk registers, qualitative and quantitative risk analysis, layers of protection analysis (LOPA), critical controls verification and much more!
Ready to see more? Visit our Risk Management page to request a demo with one of our customer solutions consultants today!
